Visualizing Code in Eclipse (Using Architexa)

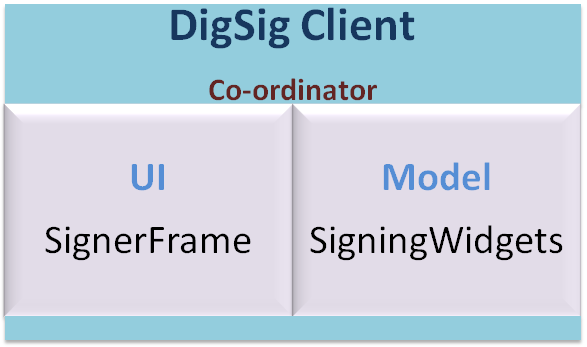
I am here sharing a nice tool I recently found to draw the diagrams for my final year project at university. When the project is concerned, managing it is challenging with, code base of the project is pretty large a team is working on the project we need to maintain the quality and performance of the project proper documentation is also evaluated So we were searching for an easy to use and nice looking tool to achieve the purposes without making it annoying that, we can focus more on the logic and optimization than decorating a diagram. :) That is were I found this plugin for eclipse called Architexa client, which is free for use. Following is a sequence diagram I generated using the plugin, which didn't take more than 30s to draw than dragging the relevant classes and setting the relevant calls. Following is a class diagram generated, that you can clearly observe the clear and smart look of the diagrams. Pros: From several t...