Apache Wookie W3C Widget Digital Signature Implementation - GSoC2012
I am here sharing my GSoC 2012 project details which I enjoyed a lot while learning. This includes a brief introduction on the project with it's design, implementation and guidance on using. The implementation has been done using Apache Santuario 1.5.2 release to generate digital signatures. The project is mentored by Scott Wilson who was so helpful and supported by the community. This is Scott Wilson's post on the project.
What is Apache Wookie?
Apache Wookie is a Java server application that allows widget uploading and deployment as useful for variety of applications. This may include gadgets to quizzes and games. Wookie has been based on W3C widget specification while providing flexibility on Google Wave gadgets etc. At the moment of writing, it is in the Apache incubator getting ready to graduate as an Apache Project.
Objective of the project
The objective this project is to implement the 'W3C XML Digital Signatures for Widgets' specification in Wookie which has been reported as a new feature. This means automating the widget upload and deployment in a secured manner without having an administrator to approve each widget. If a widget store or an author is trying to deploy a widget, Wookie needs to be capable of ensuring whether it's a trusted party and let deployment or avoid it as suitable.
Design
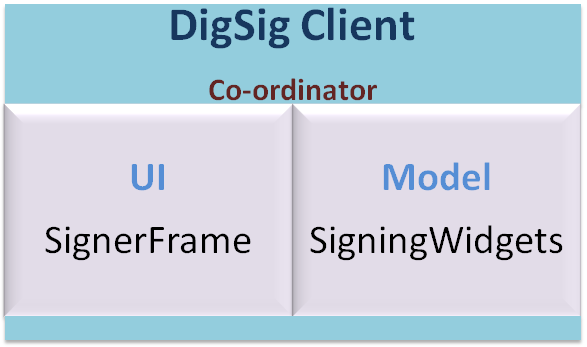
The best way to achieve this is letting the widgets' content be digitally signed and verifying the signatures at Wookie before deployment. In the way basic security needs of integrity and non-repudiation can be achieved according to W3C XML digital signature for widgets specification. So a new module has been introduced to Wookie as digsig-client to allow authors and distributors to sign the content of widgets. It provides a user friendly Java Swing UI to get the inputs from the signer. Then process them according to the W3C spec and package into a .wgt ready to be deployed in Wookie server. The client is developed according to Model View pattern separating the signing logic and UI having a coordinator among them.
Then the administrators are allowed to set up the security level of the server whether to reject the widgets that do not submit a valid signatures or to allow them under a warning.
Implementation
Signing
The signature is generated according to the exact details specified in the spec as,
- Signature algorithm - is RSA using
the RSAwithSHA256
- Key length - for RSA is
4096 bits.
- Digest method - SHA-256.
- Canonicalization algorithm - Canonical
XML Version 1.1 (omits comments)
- Certificate format - X.509
version 3
Implementation has been done using Apache Santuario 1.5.2 release. To achieve the highest possible security, the public key certificate of trusted signers needs to be imported to the trusted keystore of Wookie. You can access the code at current SVN of Apache Wookie which can be used to generate a detached signatures on any other content too.
Verification
Wookie supports 2 methods of widget deployment that,
- Drop .wgt into /deploy
- POST with attachment to /wookie/widgets
Widgets sent-in both ways are verified in the same manner starting from W3CWidgetFactory class. It bends the flow through DigitalSignatureProcessor class if the signature verification is turned on in widgetserver.properties file. The processor identifies the signature files inside the widget and try to verify each extracting the relevant public key certificate from Wookie trusted store. According to the settings at widgetserver.properties, it decides whether to reject widget or deploy with a warning in case of a invalid widget found.
In the processor it,
- Check for presence of signature file,
- Categorize them as author or distributor to understand the which content should be addressed in signature,
- Check whether all content is signed according to the W3C widget digsig spec.
- Retrieve trusted public key certificate from Wookie trussted keystore
- Throws exceptions or put warnings when invalid signatures are encountered
- handle widget deployment accordingly
You can access the code at current SVN of Apache Wookie.
Usage
When the digsig-client is run it will show up a Swing UI as follows.
The relevant steps for generating key pairs needed for digital signatures and procedure to import public certificates can be found in this post.
Enjoy with Wookie...............!
- Have to select the role of the signer whether author or distributor
- Then should point to the keystore which stores the relevant private key
- It's password should also be given followed by private key alias
- Then if private key password is same as the keystore password and certificate alias is same as private key alias you can leave it blank.
- Then once you select the widget folder from the file chooser, digsig-client will show the files selected to be signed from the widget according the role. This will automatically skip files starting with '.' and signature files as mentioned in the W3C spec.
- Then you can give the name of widget
- Once signed the <name>.wgt file is stored in the widget path including signed content and generated signature file, being ready to send to deployment as follows.
In Wookie Server side, administrators need to set the following properties according the security requirement of their context. This is located at widgetserver,properties file.
# digital signature settings # Set this property to have Wookie check widget digital signatures when # deploying a widget widget.deployment.verifysignature=true # # Set this property to determine how Wookie treats widgets with invalid # digital signatures. # # If set to true, Wookie will not deploy any widgets with invalid # digital signatures. If set to false, the widget will be imported # and a warning logged. widget.deployment.rejectinvalidsignatures=true # # If set to true, Wookie will only deploy Widgets that have valid digital signatures # AND that each signature uses a trusted certificate located in the trusted keystore, # disregarding setting the above to false. widget.deployment.rejectuntrustedsignatures=false # # Name of the trusted keystore file widget.deployment.trustedkeystore=wookieKeystore.jks #Password for the trusted keystore file widget.deployment.trustedkeystore.password = wookieAfter that Wookie server will handle the deployment of widgets in a secured manner given that the trusted public certificates are imported into the trusted keystore of the Wookie server.
Following is a sample author signature generated by digsig-client.
<ds:Signature xmlns:ds="http://www.w3.org/2000/09/xmldsig#" Id="AuthorSignature"> <ds:SignedInfo> <ds:CanonicalizationMethod Algorithm="http://www.w3.org/2006/12/xml-c14n11"></ds:CanonicalizationMethod> <ds:SignatureMethod Algorithm="http://www.w3.org/2001/04/xmldsig-more#rsa-sha256"></ds:SignatureMethod> <ds:Reference URI="build.xml"> <ds:DigestMethod Algorithm="http://www.w3.org/2001/04/xmlenc#sha256"></ds:DigestMethod> <ds:DigestValue>NWR/9AmarWLIAOFg6XHWF0Myf3MrSk+G13ioHAGHm00=</ds:DigestValue> </ds:Reference> <ds:Reference URI="config.xml"> <ds:DigestMethod Algorithm="http://www.w3.org/2001/04/xmlenc#sha256"></ds:DigestMethod> <ds:DigestValue>KhOSsl7spZ1v8ugGLy2+Pzl/Iinyv9Qwsqll60L16sw=</ds:DigestValue> </ds:Reference> . . . <ds:Reference URI="images/background.jpg"> <ds:DigestMethod Algorithm="http://www.w3.org/2001/04/xmlenc#sha256"></ds:DigestMethod> <ds:DigestValue>S02OAXynBMEK+Br9HWGaKbljDjW2I9MPAHegWePA5Gw=</ds:DigestValue> </ds:Reference> <ds:Reference URI="#prop"> <ds:Transforms> <ds:Transform Algorithm="http://www.w3.org/2006/12/xml-c14n11"></ds:Transform> </ds:Transforms> <ds:DigestMethod Algorithm="http://www.w3.org/2001/04/xmlenc#sha256"></ds:DigestMethod> <ds:DigestValue>rCbva4a0iK6CmjtYZck/3bdatRegvNe2zGi3kLDd6Yk=</ds:DigestValue> </ds:Reference> </ds:SignedInfo> <ds:SignatureValue> a7FxoERD3leteDx+jJ7xwXL8iUNC/0x6mOoS9rLOCrP0kh4tULk6zKr9XLbnv1LAVfwdJKXaVG1z IrRt3+XLspvEONIqPt8z9uZ/J9ff+/U5srt6trSbBRY/JeGGqKE5kz/0Dc3YFQzQtoWwdBR4KuMG Ghhi5X3iXDJmpgKv+C8= </ds:SignatureValue> <ds:KeyInfo> <ds:X509Data> <ds:X509Certificate> MIICSTCCAbKgAwIBAgIET78PqzANBgkqhkiG9w0BAQUFADBpMQswCQYDVQQGEwJMSzEQMA4GA1UE.................pprfWjkszI21SecAXUPiDE3yxIaEOOBOZ4EhUayH5+bE/widid76ibazpqrLzvi5V3zglTkiqrLeKN8Hdu1baRLOw== </ds:X509Certificate> </ds:X509Data> <ds:KeyValue> <ds:RSAKeyValue> <ds:Modulus> 3JwTnPNV7ZXjT4o4oKuw9OSJXxID++i5UDuceV0GKNB4pprfWjkszI21SecAXUPiDE3yxIaEOOBO Z4EhUayH5+6PVaNHo5qRZbpkL10zDCzr2efxp/3QbSnFFItn9EnRFAGvEBFdF9fOuiLNt0p2vDDm d+GLqGKv7sslRK5FcB8= </ds:Modulus> <ds:Exponent>AQAB</ds:Exponent> </ds:RSAKeyValue> </ds:KeyValue> </ds:KeyInfo> <ds:Object Id="prop"> <ds:SignatureProperties xmlns:dsp="http://www.w3.org/2009/xmldsig-properties"> <ds:SignatureProperty Id="profile" Target="#AuthorSignature"><dsp:Profile URI="http://www.w3.org/ns/widgets-digsig#profile"></dsp:Profile></ds:SignatureProperty> <ds:SignatureProperty Id="role" Target="#AuthorSignature"><dsp:Role URI="http://www.w3.org/ns/widgets-digsig#role-author"></dsp:Role></ds:SignatureProperty> <ds:SignatureProperty Id="identifier" Target="#AuthorSignature"><dsp:Identifier>test</dsp:Identifier></ds:SignatureProperty> </ds:SignatureProperties> </ds:Object> </ds:Signature>
The relevant steps for generating key pairs needed for digital signatures and procedure to import public certificates can be found in this post.
Enjoy with Wookie...............!